
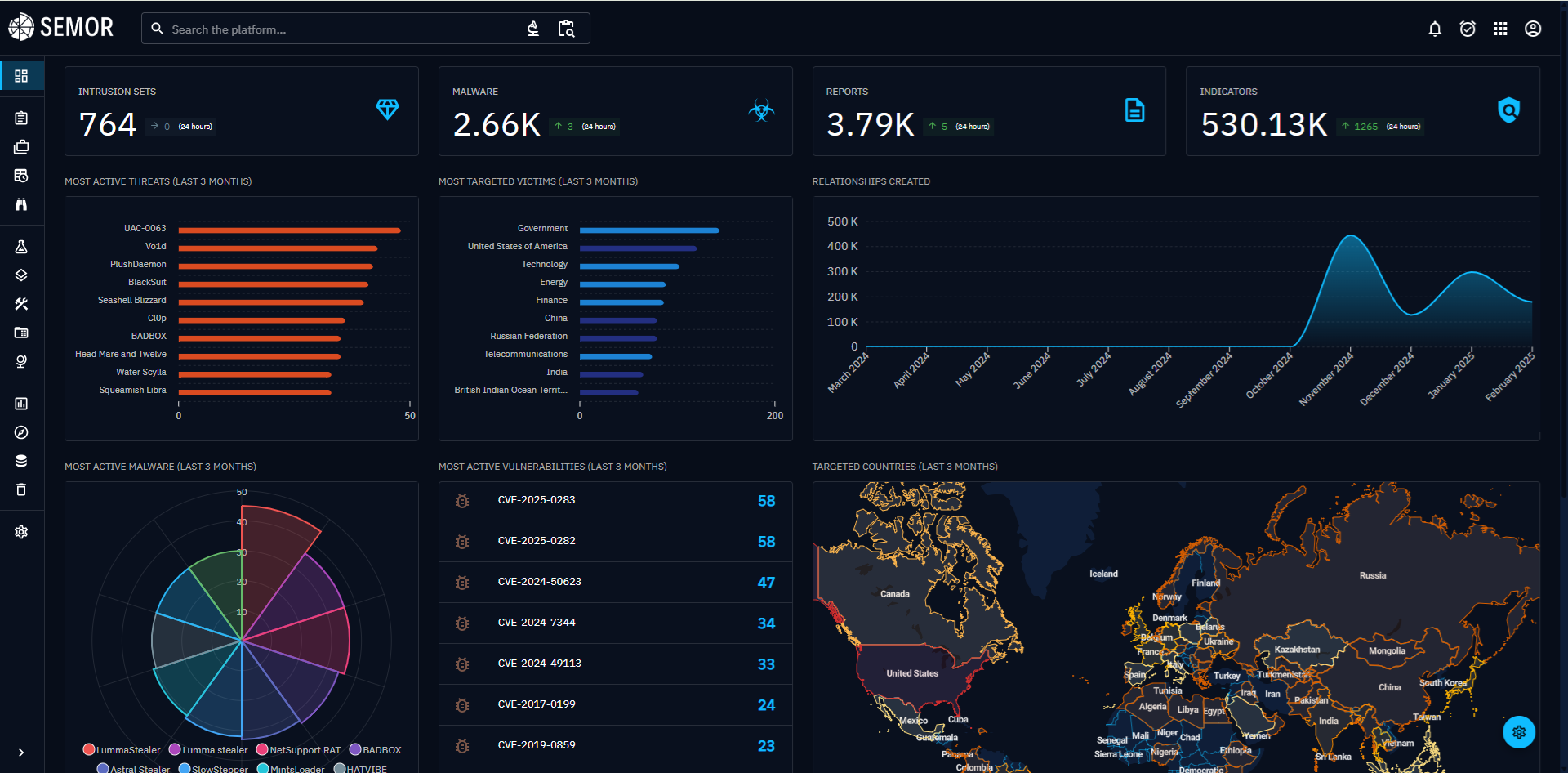
SEMOR is an integrated security operations management platform.
It consists of four main modules: SIEM (Security Information and Event Management), Remote Access Control, Network Access Control, and Cyber Threat Intelligence.
By combining these four modules, SEMOR creates a Zero Trust framework tailored to the needs of internal enterprise security. SEMOR collects information from both internal and external devices, threat intelligence, and vulnerability risks. Through correlation analysis, it helps enterprises quickly identify the source of abnormal events when they occur. In conjunction with the organization’s compliance policies, SEMOR can instantly intercept and block devices that violate policies or pose security risks, ensuring the highest level of security within the corporate network environment.
Given the frequent global cyberattacks, SEMOR’s initial goal was to develop effective defense mechanisms. Therefore, leveraging different security modules allows SEMOR to adapt to various environments and achieve optimal security for enterprise networks.
Process mechanism
The SEMOR platform is based on the following four processes to help enterprises achieve the most secure network environment architecture.
Visibility
The SEMOR platform collects all internal network information through modes such as ARP, SNMP, and FLOW, and performs visibility analysis and asset classification based on different types and connection scenarios. It can be combined with existing asset management systems for asset analysis.
Compliance
Establishing an optimal information security defense model based on compliance conditions, transparently formulating strategies, and implementing mechanisms such as identity verification to achieve a Zero-Trust security network architecture.
Instant response
Every connection must have the necessary permissions to access and manage resources. If the connection does not comply with policy requirements, it will be allocated to an isolated area or service connection will be stopped, reducing the chance of risk occurrence.
Relevance
Collect all events/logs/traffic and threat intelligence from devices. Utilize custom correlation analysis with events and logs. When abnormal events occur, the system will automatically generate alert messages and promptly send them to administrators.
SEMOR
Main functional features of security maintenance platform products
SEMOR is an integrated defense monitoring platform. It includes SIEM, Remote Access Control, Network Access Control, Performance Monitoring, and Threat Intelligence.
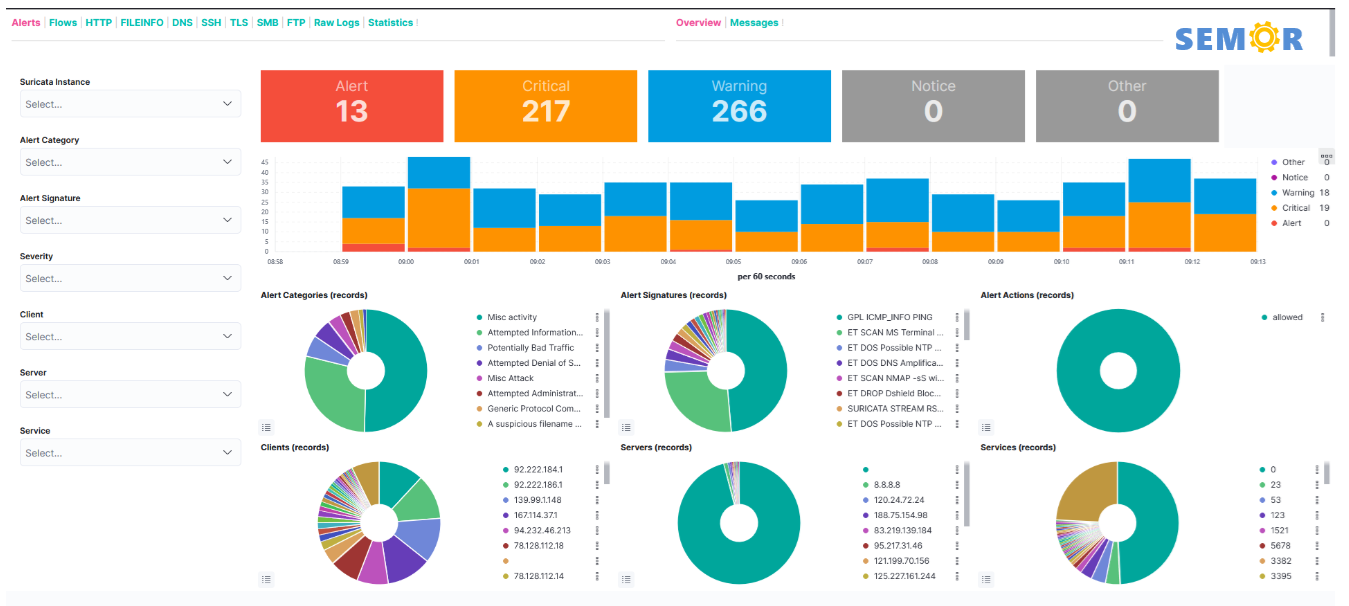
event collection and correlation analysis
- Event collection and analysis - automatically collect all records through Syslog, Event, and Flow, and identify potential threats and problems through correlation analysis
- Traffic monitoring and analysis - Analyze attack threats through traffic monitoring combined with Zeek and Suricate attack characteristics
- Real-time alerts - when attacks and threats are discovered, the system automatically alerts administrators through emails and messages
- Customized reports - In addition to the system's preset dashboards, managers can customize charts and dashboards based on queries or analysis
- AI-powered, real-time Security Information and Event Management (SIEM) - Leveraging Convolutional Neural Networks (CNN), Natural Language Processing (NLP), and advanced infrastructure components, this system provides a robust security solution that detects, analyzes, and responds to threats in real-time
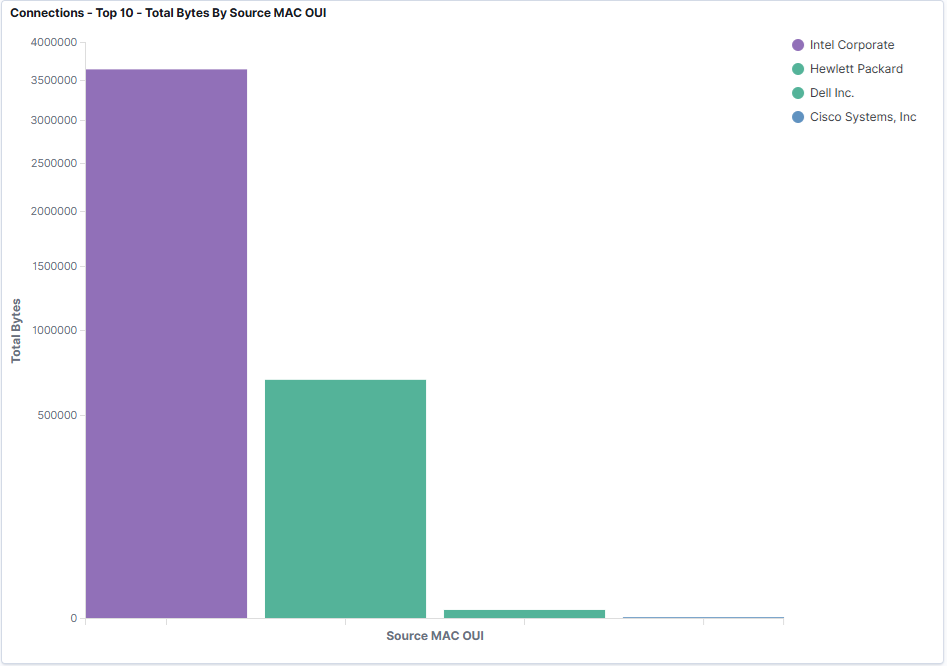
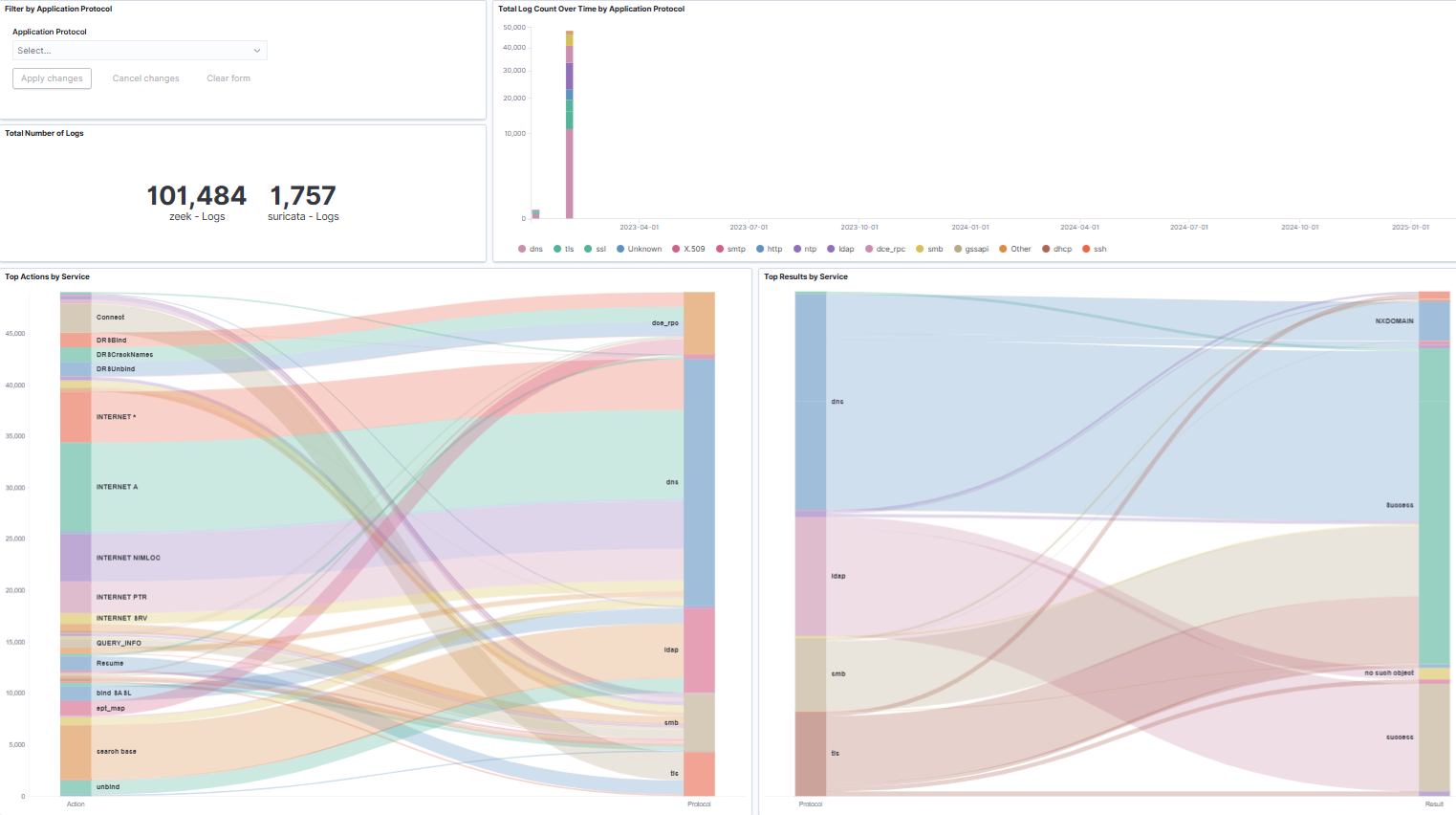
Network traffic behavior analysis
- Traffic data analysis - collect and analyze all current internal network data and device information through traffic
- Attack threat analysis - Combining Zeek and Suricate intrusion attack signature systems to compare which attacks are ongoing on the internal network
- Diversified asset analysis - Combined with the MAC manufacturer database, automatically analyze the assets and brands on the network
- Protocol Analysis - Automatically analyze all communication protocols and connections through traffic collection
- Software Analysis - Actively analyze which software is currently executing in traffic packets and whether there are potential risks
Threat Intelligence Automation integration
- Threat Hunting - Quickly search for relevant information from different sources and identify potential threats through analysis
- Threat Analysis - In-depth study of malware, IOC (Indicator of Compromise) and other malicious behaviors
- Integrate SEMOR SIEM - integrate threat intelligence directly into log management and incident response processes
- Automated workflows - use connectors to automatically capture intelligence and customize triggering logic
- Built-in multiple intelligence connectors - More than 20 built-in intelligence connectors, which can connect to external intelligence resources (such as Crowdstrike, Fortinet, Paloalto, Cisco, Cybersixgill, Kaspersky, Recorded-Future, Sentinelone) and other world-renowned intelligence resources
- System formatting standards - following STIX2.1, data is directly compatible with other STIX formatting systems
- High performance - optimized data storage and retrieval mechanism to support big data analysis and processing
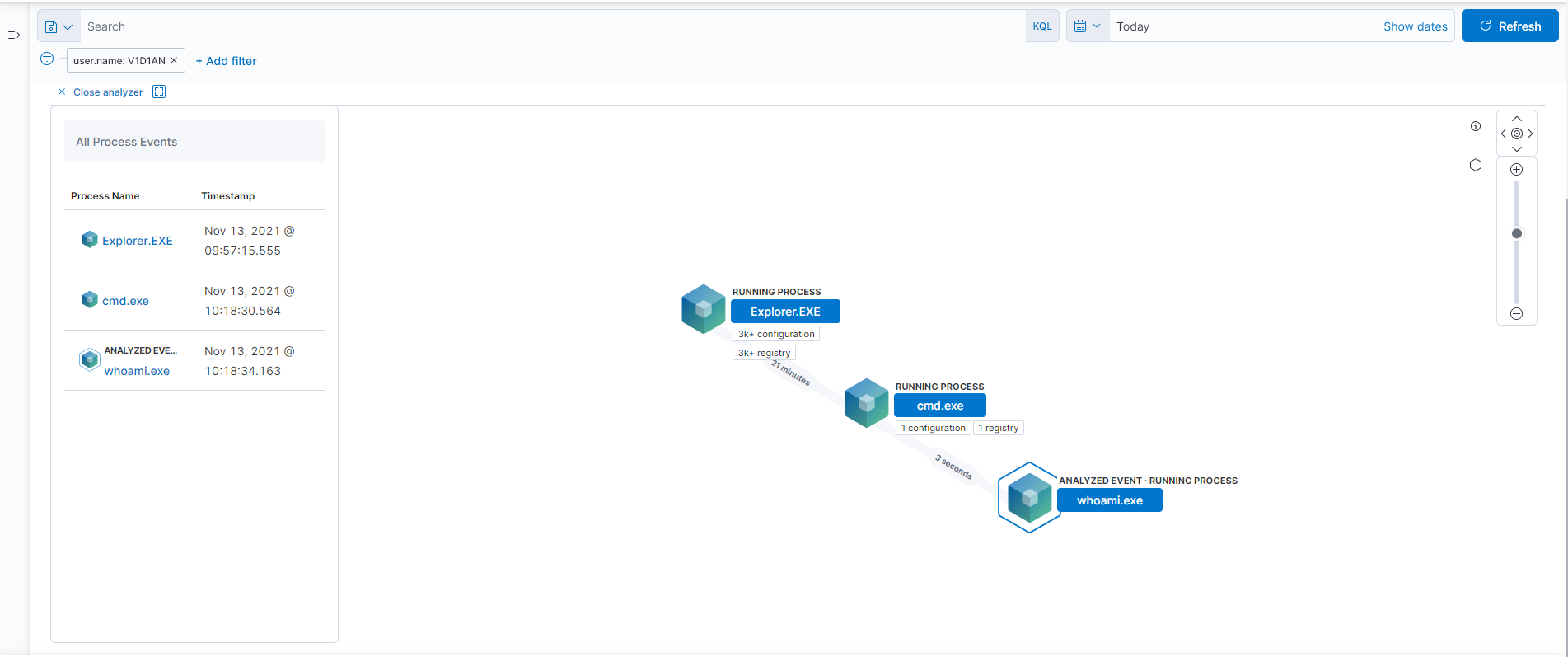
Secure Remote Access with Audit
- Provide international 4A audit standards.
- Offer equipment/account/file access permission management.
- Provide operation/command/file operation and access records.
- Enable real-time playback of video records and immediate connection interruption.
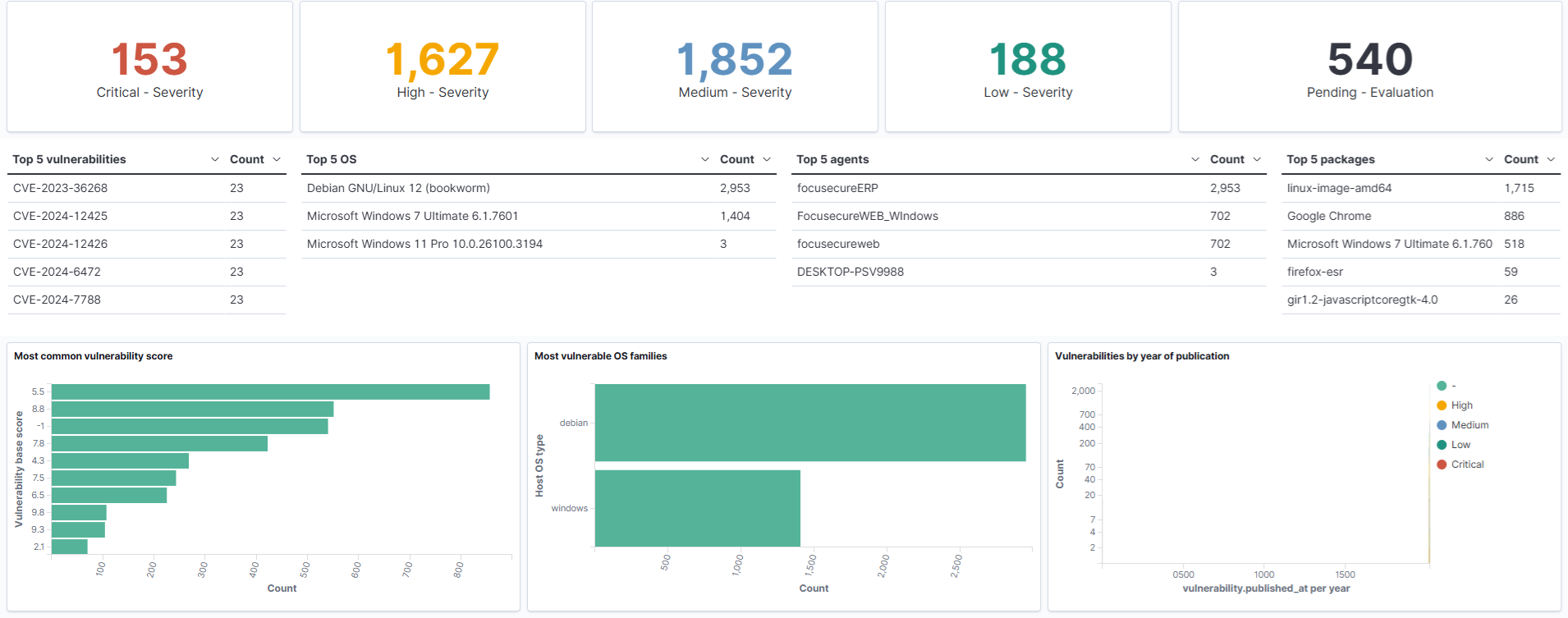
Vulnerability Assessment Risk Scoring
- Vnulnerability Analysis and Notice System - Combine asset management and vulnerability management to grasp the overall risk situation and assist agencies in implementing ISMS asset inventory and risk assessment tasks.
- Assets Risk Management System - Assess asset weaknesses and possible threats based on Confidentiality, Integrity and Availability, automatically calculate asset risks, and produce risk assessment reports that comply with regulations
- Compliance Reports - Provides international information security compliance reports. Includes PCI-DSS, GDPR, HIPPA, NITS-800, TSC and ISO-2001. The required compliance reports can be directly generated by Administrator
Main functional modules
The system model rental includes four major items: log collection and correlation analysis, secure remote access, network security access, and internal and external network threat analysis and assessment. These four modules form the foundation of a zero-trust architecture.


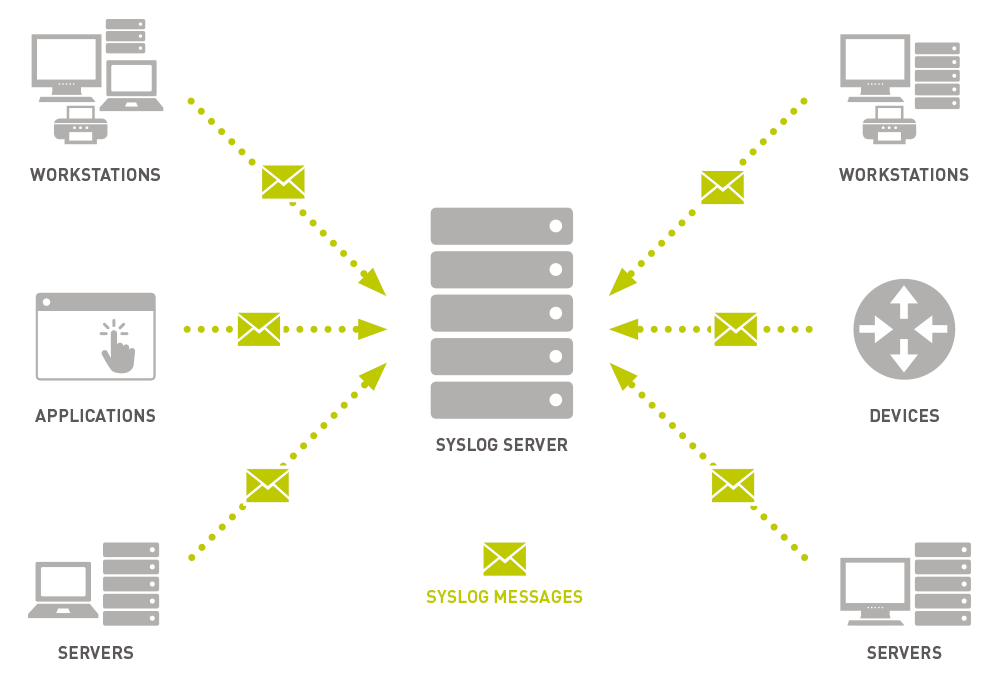
Log collection Analysis
Is composed of Wazuh and OpenSearch engine. It can collect logs, traffic, events, and more from all devices. All information can be analyzed using custom correlation analysis conditions, and relevant alarm trigger conditions can be set. When anomalies occur, the system will automatically issue alerts based on the configured policy.
Remote Access Control (RAC)
Network Access Monitor (NAM)
Network Risk Assessment
The log collection system is composed of Wazuh and OpenSearch engine. It can collect logs, traffic, events, and more from all devices. All information can be analyzed using custom correlation analysis conditions, and relevant alarm trigger conditions can be set. When anomalies occur, the system will automatically issue alerts based on the configured policy.
Relational Architecture
Through SEMOR’s platform integration, SEMOR can provide multidimensional reports for maintenance, monitoring, recording, analysis, and assessment. Users can define their own SEMOR operational platform based on their specific needs. Using an intuitive drag-and-drop interface, users can easily adjust report column order, timeframes, and other fields. This flexibility allows managers to quickly meet the requirements for job management and analysis.
External Threat intelligence
Integrating threat intelligence from the dark web, deep web, hacker organizations, public networks, and reputation organizations, and exporting it to a Security Information and Event Management (SIEM) system for consolidation.
Internal Network Event
Analyze the credentials, connection requirements, data transfer, and application service monitoring and management policies to determine the behavior of each application connection.
Correlative integration analysis
Defining, correlating, and operating on multidimensional information generated through relevant link behavior, policy execution, and event logs.


System Structure
The SEMOR platform, through its integration, provides multidimensional reporting for operations, monitoring, recording, analysis, and assessment. Users can customize their SEMOR situational platform based on their specific job requirements. With an intuitive drag-and-drop interface, users can easily adjust report column order, timelines, and other fields. This flexibility allows managers to quickly meet various needs for job management and analysis.
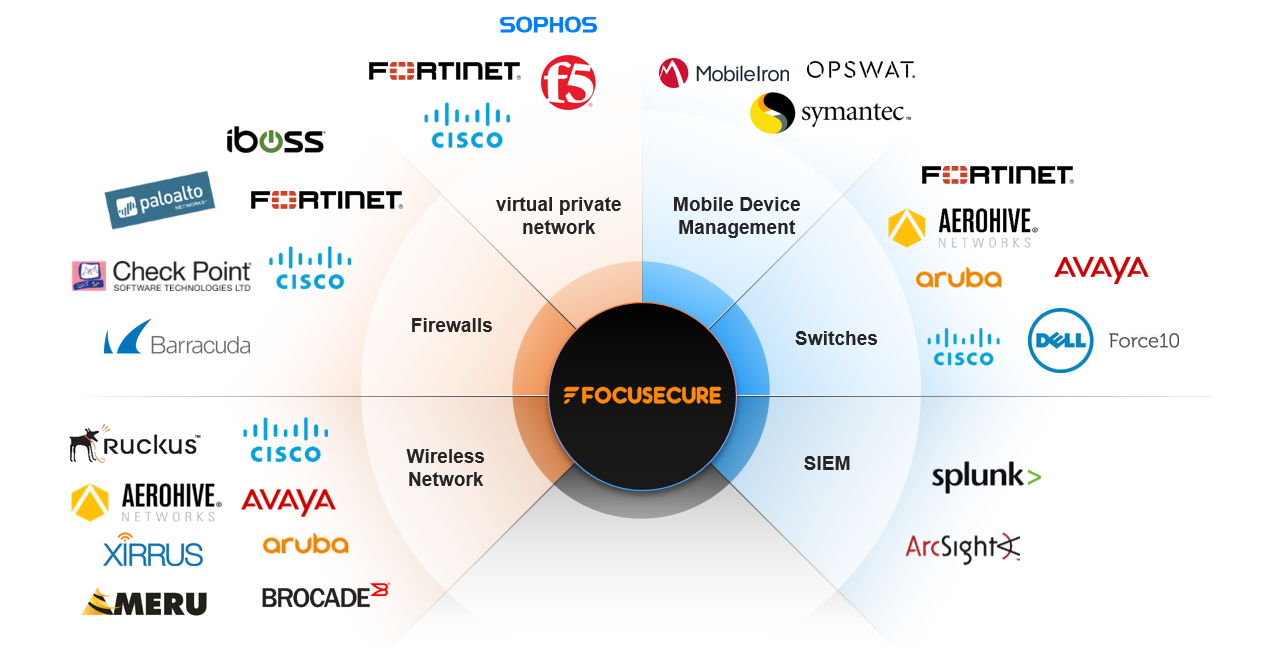
Brand Compatibility
The SEMOR integrated monitoring and defense platform is capable of integrating multiple international brands. To achieve regional collaborative defense capabilities, it integrates with systems such as firewalls and network switches. When abnormal events occur, the platform promptly communicates with defense systems to issue defense instructions. This proactive defense helps prevent attack propagation and cross-infection, ultimately reducing the workload for administrators.
Global Partners
Malaysia
Singapore
Peru
Philippines




Taiwan Partners






Welcome to Join as Our Partners
If you are interested in our solutions, we welcome you to contact us anytime to learn about our products or join our distribution partners.
SG: +65 8067 4725
TW: +886 2 2595 4260
MY: +60 16 982 6311
Latest News

Sincerely invite all friends who care about cybersecurity and embrace innovation to join us in...

FOCUSECRE SEMOR’s first promotional video has been officially released. The content will provide a...

Every year, the annual cybersecurity event, CYBERSEC 2024 Taiwan, is set to take place in May....



